Each vulnerability in the KnowledgeBase is assigned a ID (QID). Additional information for classification and tracking is provided.
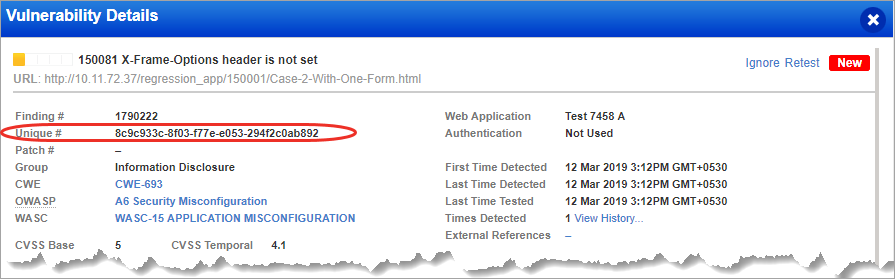
We assign 36-bit unique ID (uniqueId) for each finding. The ID is unique for every finding. Earlier, the combination of three fields namely: finding ID (QID), finding type and finding category would make a finding unique. The implementation of uniqueId helps you easily distinguish every finding. Show me
For each vulnerability detected, we provide descriptions to help you identify and remediate the issue. The Threat section shows a description of the security threat associated with the vulnerability. The Impact section gives a description of the possible consequences that may occur if the vulnerability is successfully exploited. The Solution section provides a suggested solution to fix the vulnerability. This may include a link to a patch, update, the vendor's Web site or a workaround.
CVE ID - The CVE name(s) associated with this vulnerability check. CVE (Common Vulnerabilities and Exposures) is a list of common names for publicly known vulnerabilities and exposures. Through open and collaborative discussions, the CVE Editorial board determines which vulnerabilities or exposures are included in CVE.
Bugtraq ID - This is the number assigned to the vulnerability by SecurityFocus, a vendor-neutral web site that provides security information to members of the security community.
Vendor Reference - A reference number released by the vendor in regard to the vulnerability, such as a Microsoft Security Bulletin like MS03-046. This may be a link directly to the vendor's web site.
CWE ID - The CVE name(s) associated with this vulnerability check. The Common Weakness Enumeration (CWE) is a list of common names for publicly known software security weaknesses.
OWASP - The OWASP name(s) associated with this vulnerability check. The Open Web Application Security Project (OWASP ) lists the most critical security risks to web applications.
WASC - The WASC name(s) associated with this vulnerability check. The Web Application Security Consortium (WASC) is a list of open source and widely agreed upon best-practice security standards for the World Wide Web.
This tells you the scanning method required to discover the vulnerability. This may be:
- Remote only (remote unauthenticated scanning is required for detection)
- Authenticated Only (authenticated scanning is required for detection)
- Remote and Authenticated (remote scanning or authenticated scanning is required for detection)
This tells you the whether authentication is required to detect the vulnerability. If authentication is required, we'll list the authentication methods that must be used: Windows, Unix, Oracle, SNMP, VMware, DB2, HTTP, Form.
It's easy. Just enable the CVSS Scoring feature within the VM application. Go to VM/VMDR > Reports > Setup > CVSS (Manager role is needed). Once enabled, CVSS values are displayed for confirmed and potential vulnerabilities (they are not shown for Information Gathered). Learn more
CVSS Base and CVSS Vector String are provided by NIST, unless it marked with a footnote [1]. The footnote means the score is provided by our service. CVSS Vector String is a combination of CVSS V3 metrics and their values as assigned to the vulnerability.
CVSS Temporal score is provided by our service.
Check out: Exploitability | Malware | Compliance