Manage all your detections in one place. The detections tab acts as a central area for application security vulnerability detections, management and information. We list all your findings (Qualys, Burp, and Bugcrowd) in the Detections tab.
Does the status of the detection change when it isn't found during a scan? |
|
|
Detections tell you about security findings discovered by our cloud security service. These are based on your most recent scans. To review your current detections, go to Detections > Detection List. You can sort detections by web application or filter the list numerous ways - by tags, scan date, severity and more.
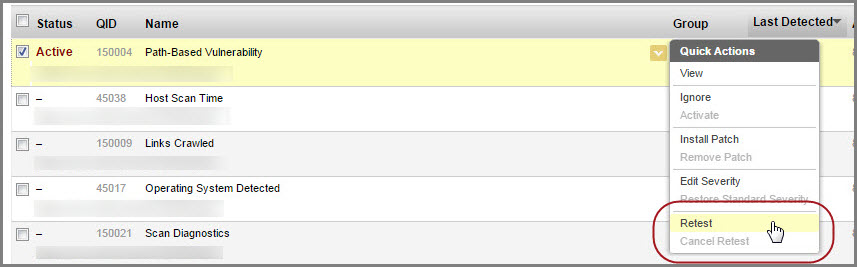
Yes, you can easily retest the findings for individual vulnerabilities by launching a scan to test the selected finding. Only potential vulnerabilities, confirmed vulnerabilities and sensitive contents are available for retest.
In the Detections tab, just navigate to the vulnerability you want to retest and click Retest from the Quick Actions menu. Once the retest is finished the updated details are displayed for that vulnerability. Look here
If the URL of your web application changes, it is recommended to create a new web application with the new URL and execute a scan to know the detections rather than conducting a retest. However, if you need to retain the web application and update the URL, then it is recommended that you purge all detections on the web application and run a scan before you proceed for the retest.
Yes, you can easily retest the findings for vulnerabilities by launching a scan to test the selected multiple findings. Only potential vulnerabilities, confirmed vulnerabilities and sensitive contents are available for retest. You can club the multiple findings that belong to the same QID and web application and launch a retest in a single batch. The retest scan uses same settings used in the latest scan. If you cancel the retest for any of the findings, the retest scan is cancelled for the entire batch of findings.
Go to Detections > Detections List. You can use filters in the left-pane to view all findings of same QID and web application. Select the findings to be retested. From the Actions menu, select Retest. Once you confirm, the retest scan would be launched on all the selected findings at one go. Show me
Double click a detection row, or hover over the row and choose View from the menu. Learn more
You can do this by marking those detections as ignored. Hover over the detection row (vulnerability or sensitive content) and choose Ignore from the menu. When you ignore a detection, you'll be prompted to give a reason - false positive, acceptable risk or not applicable. The status label is grayed out in the list and, by default, the detection will not appear in future reports on the same web application. Learn more
Want to reactivate an ignored detection? Just choose Activate from the Quick Actions menu.
Can I schedule reactivation of a detection?
Want to see the flow? Look here
New - The first time a vulnerability is detected by a scan the status is set to New.
Active - A vulnerability detected by two or more scans is set to Active.
Fixed - A vulnerability was verified by the most recent scan as fixed, and this vulnerability was detected by the previous scan.
Reopened - A vulnerability was reopened by the most recent scan, and this vulnerability was verified as fixed by the previous scan. The next time the vulnerability is detected by a scan, the status is set to Active.
Protected - A vulnerability that is blocked for an application protected by WAF.
Retesting - A vulnerability that is being retested.
The groups column identifies the group each detection belongs to.
For vulnerability detections, XSS appears for cross-site scripting vulnerabilities, SQL for SQL injection vulnerabilities, INFO for information vulnerabilities and PATH for path-based vulnerabilities.
For sensitive content detections, CC appears for credit card number detections, SSN for social security number (US only) detections, CUSTOM for custom (user-defined) sensitive content detections.
For information gathered, IG_DIAG for diagnostic IG (general information about the scan), IG_WEAK for weakness IG (issues that are security weakness or conflict with best practices) detections.
The detection age calculated based on the First detected date, that is, when the vulnerability was detected the first time.
Each detection is assigned a severity level that tells you the security risk associated with its exploitation. Learn more
Yes, you can easily customize the severity of findings (vulnerability/sensitive content/information gathered) reported in your web applications. Learn more
Yes, you can export detection details to your local file system in HTML format. Just click the Export icon in the payload response section. Show me
The preview pane appears below the list when you click in a detection row. The preview displays the QID and severity level of the vulnerability along with detection details. Show me
Do you have WAF in your account? If yes, you can use WAF to protect against vulnerabilities by installing virtual patches. Go to WAS > Web Applications > Detections. Identify the detection you want to patch (vulnerability or sensitive content) and choose Install Patch from the Quick Actions menu. Review the patch details and feel free to update or remove rule conditions. Then click OK. We'll add a virtual patch rule to your firewall.
Manager users have full rights to manage remediation tasks. For other users their assigned roles and permissions determine whether they have WAS Remediation Permissions (i.e. ignore findings, retest vulnerabilities and sensitive content, update findings). To see a user's assigned roles, go to the Administration utility (select from the application picker) and view/edit the user of interest. Learn more
We have filters to enhance the search and quickly locate the detection type. In addition to the common filters, depending on your finding type, more filters specific to each finding type are displayed. For example, if you choose Finding Type as Burp, then filters that are applicable for Burp related findings are enabled and the other non-applicable filters are disabled.
You can distinguish the finding type with the icon displayed in the list.
 - Qualys detections
- Qualys detections
 -
Burp detections
-
Burp detections
 - Bugcrowd
detections
- Bugcrowd
detections
Additionally, you can fasten your search, by directly using filters for QID or finding ID.
We have now made external references for QID available to all by default. You could add any external references such as IDs, comments or any other reference you want to associate with the QID. You can now add and view external references that are added to a QID or search for QIDs with specific external references.
Go to Detections > Detection List, pick the QID you would want to add external references to and then select External References from the quick action menu. Type the content you want to add in New Reference and then click OK. You could add upto maximum 10 references for a QID. Use the Delete link to remove the reference associated with the QID. Show me
To view the references associated with a QID, go to Detections > Detection List, pick the QID and then select view from the quick actions menu. The QID details now lists the external references associated with the QID. If there are multiple references, click more link to view all the references. Show me
We have also added a new filter to ease your search for a QID using the external references you add to a QID. Show me
By default, the status of a detection won't be changed when the vulnerable URL of the detection isn't found anymore during a scan. There exists a per-customer configuration option to have this behavior changed. You need to send a request to your TAM or Qualys Support if you want to have this feature for your subscription. After the setting is enabled for your subscription, the detection status will be changed to "Fixed" when the vulnerable URL is not found in the scan.